by Bruce Aboudara on July 2017
IT security is a complex and very broad topic that requires multiple elements of an organization working well together. At the systems level you must consider business, information, data and solution architectures. Next there are all the process designs that overlay these systems. Therefore just being able to collect, patch and provide device vulnerability data should not be considered protecting against a ransomware attack. That instead requires a layered security approach that can anticipate and thwart these attacks.
In the ISO 27001 ISMS Security Architecture, Asset Management has as key role to play in this layered security approach. ITAM addresses asset inventory, standards, and procedures. Fundamental to ITAM is discovery and understanding your vulnerability based on a detailed workstation vulnerability analysis. Included in this analysis is patch status, anti-virus and anti-malware status and then a calculation of a security assessment based on a variety of inputs.
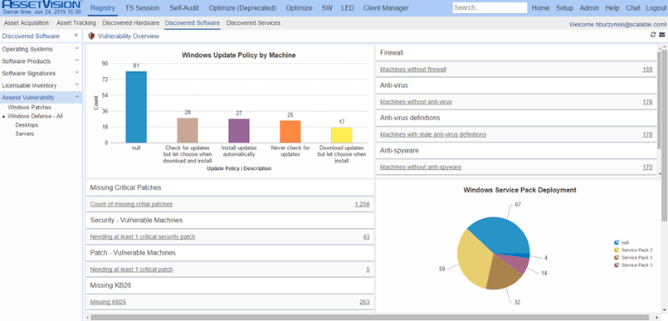
Since 2013 Asset Vision has had just these types of capabilities for Windows machines and our users can scan and collect this data using our wide array of agentless probes. The results are displayed in standard dashboard showing patches and update policies such as the one shown below.
A device vulnerability dashboard like this contains essential elements such as:
- Windows Update Policy by Machine
- Security Gauge Set which contains counts of firewall and anti-virus software
- Vulnerability Gauge Set showing counts of missing security patches
- Windows Service Pack Deployment with counts of Windows Services Packs, grouped by the service pack number
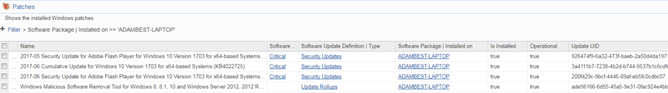
Now, for the specific case of ransomware, one is generally concerned with making sure that the proper patches are installed. Another view of data collected by Asset Vision displays device Windows patch status of machines scanned by the OS System Patches probe along with the specific KB numbers.
How Can ITAM Help?
However the role that ITAM can play in assessing device vulnerability is broader than just a probe to detect a specific KB entry that is assigned to a particular ransomware bit of code. Instead it is to provide a more holistic approach to properly discovering and reporting on the IT assets that are likely to be targeted with the many types of malware, viruses and other nasties trying to penetrate corporate networks on a daily basis.
Scanning devices for patch status, implementing trusted or untrusted software policies, and searching unauthorized software are some functions up-to-date, modern discovery tools can provide. They are critical capabilities of any well-conceived, multi-layered security architecture. However, ransomware can in its own right be a trojan horse. As seen with recent attacks involving cyber weapons stolen from the N.S.A. such as EternalBlue and DoublePulsar where ransomware was the distraction to load other malicious code into a network, cyber security is a daunting and minute-by-minute IT role that needs all elements working together.